Domain Naming Service (DNS)
Securing your web surfing.
We, as users, take simple things such as google.com and espn.com for granted. One of the most important aspects of cyber security is protecting our ability to find and navigate websites safely. While a VPN secures your connection and content to the website, a user still needs to know where the website is in cyberspace. A malicious internet connection can hijack your ability to access a legitimate website such as google.com by telling your computer that Google.com is a site they control. To protect against redirection and rebinding of websites, we need to ensure we trust where we directions to a website.
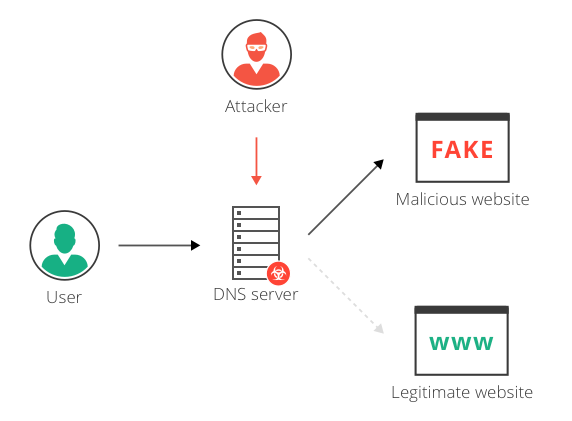
How we get to websites.
The internet runs on numbers and IP addresses such as ‘66.249.64.2’. This set of numbers is like a street address in cyberspace telling your computer where to go for the content on the internet you want. Your computer reaches out and makes a connection, and you get the required content. It would not be very pleasant to know all those numbers to access the hundreds of websites we access daily. Instead, We rely on the Domain Naming Service to get access to the websites we want.
What is the Domain Naming Service (DNS)
The process of DNS resolution involves converting a website (such as www.espn.com) into a computer-friendly IP address (such as 66.249.64.2). An IP address is given to each device on the Internet, and that address is necessary to find the appropriate Internet device – like a street address is used to find a particular home. When a user wants to load a webpage, they must translate what they type into their web browser (example.com) and the machine-friendly address necessary to locate the example.com webpage.
~Cited https://www.cloudflare.com/learning/dns/what-is-dns/
Common types of DNS Attacks
A malicious actor has a couple of methods that are the primary threat to us as users. Below is not the entire list by any means.
DNS spoofing/cache poisoning: This is an attack where forged DNS data is introduced into a DNS resolver’s cache, resulting in the resolver returning an incorrect IP address for a domain. Instead of going to the correct website, traffic can be diverted to a malicious machine or anywhere else the attacker desires; often, this will be a replica of the original site used for malicious purposes such as distributing malware or collecting login information.
DNS hijacking: The attacker redirects queries to a different domain name server in DNS hijacking. This can be done either with malware or with the unauthorized modification of a DNS server. Although the result is similar to that of DNS spoofing, this is a fundamentally different attack because it targets the DNS record of the website on the nameserver rather than a resolver’s cache.
~Cited https://www.cloudflare.com/learning/dns/dns-security/
DNS Attacks Defense
If DNS is our mapping service of the Internet, then we need to protect our request for directions so that a hacker does not know where we are going and gives us bad directions. By default, DNS queries and responses are sent in unencrypted, human-readable format, which means they can be read by networks, ISPs, or anybody able to monitor transmissions. Even if a website uses HTTPS, the DNS query required to navigate to that website is exposed.
This lack of privacy has a huge impact on security and, in some cases, human rights; if DNS queries are not private, it becomes easier for governments to censor the Internet and for attackers to stalk users’ online behavior.
To hide our request for directions, we need to use DNS over TLS (DoT) or DNS over HTTPS (DoH). These two standards are for encrypting plaintext DNS traffic to prevent malicious parties, advertisers, ISPs, and others from being able to interpret the data.